The location details of the workshop are provided below.
Detailed Program
Below is the tentative schedule of talks, which includes time for questions.
8:30am - 8:45am: Breakfast
8:45am - 10am Stephanie Forrest (Keynote Speaker) Biodesign Institute at Arizona State University Title: The Complex Science of Cybersecurity Abstract:
Securing today's cyberinfrastructure will take more than piecewise technical improvements to our software/hardware base. Today's systems have many features of complex systems, including: arms races with adversaries and competitors, unanticipated behaviors due to nonlinear interactions, inadvertent evolution through individual actions, and network effects. Further, the different actors in the system operate under mixed incentives---financial, political, and technical. Many complex systems face similar problems, whether it is individual bodies coping with cancer, populations of individuals that are ravaged by novel diseases, or social systems attempting to control criminal behavior. Studying the general principles that complex systems use to manage such threats can suggest techniques for tackling the problem of cybersecurity. The talk will review some of the speaker's earlier work and discuss how using the tools of complexity science to understand today's technological networks and their linkages to human behavior, social norms, and economic incentives can help us address the global scale of today's many cybersecurity problems.
10am - 10:30am Cynthia A. Phillips Sandia National Laboratories Title: Cicada: Player-Scalable, Fault-Tolerant Secure MultiParty Computation Abstract:
The published state of the art for Secure MultiParty Computation (MPC) handles single-digit numbers of players. Although some MPC approaches are theoretically fault-tolerant, current implementations cannot tolerate fail-stop faults such as processes dying. Motivated by missions that require hundreds of players implemented on unreliable hardware, we present Cicada, an open-source, fault-tolerant MPC framework written in Python. Cicada is a true multi-protocol toolkit, allowing programs to use multiple MPC protocols simultaneously at runtime. We will describe one of Cicada’s algorithmic kernels: dense matrix multiplication. This kernel has optimal communication complexity when amortized over many runs, and it works with O(100) players.
10:30am - 11am Aniket Kate Department of Computer Science, Purdue University, and Supra Title: Mitigating Collusion in Secure Distributed Computing Abstract:
A long line of research on secure distributed computing (SDC) confirms that anything that can be computed, can be computed securely using a set of non-colluding parties. Indeed, this non-collusion assumption makes a number of problems solvable and reduces overheads for several others. As a result, it is pervasive across different security systems. However, this assumption remains highly susceptible to covert, undetectable collusion among computation parties. In a series of works, we take early steps towards weakening this assumption across SDC applications. This talk describes novel mechanisms for relaxing the non-collusion assumptions in SDC assuming computation parties are rational. We will present practical incentive structures and modules for gathering and verifying collusion evidence for two prominent SDC protocols: multi-server private information retrieval (PIR), and threshold information escrow (TIE) services. The talk is based on my co-authored papers from IEEE S&P 2024 and IEEE CSF 2023.
11am - 11:30am Costas Busch Department of Computer and Cyber Sciences, Augusta University Title: Scalable Fault Tolerant Consensus for Blockchains Abstract:
We present Hermes, a consensus protocol for permissioned blockchains suitable for controlled environments. Hermes is Byzantine Fault Tolerant (BFT) and it tolerates a constant fraction of the nodes being Byzantine (malicious). A typical approach for implementing BFT consensus is to have a primary node to propose a block and letting the remaining nodes verify the validity of the block. The performance of such consensus protocols is highly dependent on the primary node. A slack primary (with limited bandwidth), even being honest, can adversely affect the performance. Hermes decreases the protocol dependency on the primary node and minimizes transmission delay induced by the slack primary while keeping low message complexity and latency with high scalability. Hermes achieves these improvements with the use of an impetus committee for accepting new blocks, having only two phases of communication per block, and by relaxing strong BFT agreement (safety) guarantees only for a specific type of Byzantine faults called equivocated faults. We analyzed the correctness of Hermes formally and also tested its performance experimentally where we showed that in the presence of slack nodes Hermes outperformed the state-of-the-art BFT protocols.
11:30am - Noon Gokarna Sharma Department of Computer Science, Kent State University Title: Blockchain in Partitionable and Dynamic Networks Abstract:
This talk addresses blockchain operation in critical conditions of partitioning and high dynamism. We focus on two blockchain consensus problems: partitionable blockchain consensus and consensus in dynamic networks. For both problems, we discuss impossibility boundaries and necessary conditions for the existence of solutions. Then, we present the algorithms that solve the two problems and evaluate the efficiency of their operation. We conclude by discussing future research directions opened by these developments.
Noon - 1pm: Lunch
1pm - 1:30pm Carolyn D. Mayer Sandia National Laboratories Title: Beaver Triples On-the-Fly Abstract:
Secure Multiparty Computation (MPC) allows for a group to perform joint computations on distributed private inputs. However, many MPC protocols rely on auxiliary inputs called ``Beaver triples'' to perform multiplications of secret values. These triples are communicationally expensive to generate, and consequently, are often precomputed. We will discuss work in progress for a method to enable on-the-fly Beaver triple generation. This work was supported by the Laboratory Directed Research and Development program at Sandia National Laboratories, a multimission laboratory managed and operated by National Technology & Engineering Solutions of Sandia, LLC, a wholly owned subsidiary of Honeywell International Inc., for the U.S. Department of Energy's National Nuclear Security Administration under contract DE-NA0003525. SAND2024-05506A
1:30pm - 2pm Nick Pattengale Sandia National Laboratories Title: Internet Infrastructure for the (near) Future Abstract:
More recent cryptographic and distributed systems primitives, such as from secure multiparty computation and distributed ledger technology, have yet to realize mainstream adoption in comparison to older primitives such as asymmetric encryption and name resolution. We suspect this won't be the case for long, as these recent primitives can enable characteristic advancement, including on the internet at large, in areas such as shared computation on sensitive data (without divulging that data), and in stronger notions of shared state across information systems. In this talk, we describe our attempts over the past decade to apply these primitives to various (typically, high consequence) use cases, and couch the lessons learned in terms of envisioned internet infrastructure of the future. Our use cases tend to provide a contrast to industry use cases, which raise interesting economic considerations (systems based on incentivization, versus resembling a public good), and game-theoretic considerations (relative to the contrast between low/high consequence use case domains).
2pm - 2:30pm Valerie King Department of Computer Sciences, University of Victoria Title: Self-discovery vs reliance on the Byzantine crowd. Abstract:
This talk explores a novel model introduced by Augustine et al. in which the goal is for a set of k machines to learn a function on n bits. We assume that knowledge may be acquired by a machine through direct expensive query of a bit or through cheaper (or even free) communication with other possibly Byzantine machines. In this case, the expensive queries serve two purposes: to verify the claimed value of a bit and to determine the honesty of a machine.
2:30pm - 2:45pm: Coffee Break
2:45pm - 3:15pm Peter Robinson Department of Computer and Cyber Sciences, Augusta University Title: Faster consensus when the adversary is late Abstract:
Distributed consensus is a fundamental problem in fault-tolerant networks with numerous applications, ranging from distributed databases to coordination tasks. In this talk, we consider the consensus problem in a synchronous system under an adaptive adversary that has a slightly outdated view and can perform a denial-of-service attack against a constant fraction of the nodes in each time step. We will look at a simple communication-efficient consensus protocol that allows us to circumvent existing impossibility results, discuss some algorithmic limitations, and give an outlook on open research questions in this area.
3:15pm - 3:45pm Varsha Dani Golisano College of Computing and Information Sciences, Rochester Institute of Technology Title: Fraud Detection for Random Walks Abstract:
Traditional fraud detection is often based on finding statistical anomalies in data sets and transaction histories. A sophisticated fraudster, aware of the exact kinds of tests being deployed, might be difficult or impossible to catch. We are interested in paradigms for fraud detection that are provably robust against any adversary, no matter how sophisticated. In other words, the detection strategy should rely on signals in the data that are inherent in the goals the adversary is trying to achieve. Specifically, we consider a fraud detection game centered on a random walk on a graph. We assume this random walk is implemented by having a player at each vertex, who can be honest or not. In particular, when the random walk reaches a vertex owned by an honest player, it proceeds to a uniformly random neighbor at the next timestep. However, when the random walk reaches a dishonest player, it instead proceeds to an arbitrary neighbor chosen by an omniscient Adversary. The game is played between the Adversary and a Referee who sees the trajectory of the random walk. At any point during the random walk, if the Referee determines that a specific vertex is controlled by a dishonest player, the Referee accuses that player, and therefore wins the game. The Referee is allowed to make the occasional incorrect accusation, but must follow a policy that makes such mistakes very unlikely. The goal of the adversary is to delay the cover time, defined as the number of timesteps until all vertices of the graph have been visited at least once. We consider the following basic question: how much can the omniscient Adversary delay the cover time without getting caught? Our main result is a tight upper bound on this delay factor. Joint work with Tom Hayes, Seth Pettie, and Jared Saia.
3:45pm - 4pm Jacob Hobbs Department of Computer Science, University of New Mexico Title: Veritas non sequitur: Why exponential strategies suffer in FlipIt Abstract:
FlipIt is a well-known cybersecurity game that employs the concept of "stealthy" moves. While it has been shown that under certain circumstances, periodic strategies are optimal, exponentially distributed moves are also considered to "work well" because they are memoryless. In this talk, I will discuss size bias and why it dooms the exponential distribution from being a logical choice when playing FlipIt.
4pm - 4:15pm Maxwell Young Department of Computer Science and Engineering, Mississippi State University Title: Bankrupting DoS Attackers Abstract:
We will present algorithms that employ resource burning (RB) to defend against denial-of-service (DoS) attacks. RB is the verifiable expenditure of a resource, such as computational power, required from clients before receiving service from the server. We show that the algorithmic cost of our defense -- the cost to both the server and the honest clients -- is bounded as a function of the attacker's cost. We model an omniscient attacker, and a server with access to an estimator that estimates the number of jobs from honest clients in any time interval. We examine two communication models: an idealized zero-latency model and a partially synchronous model. Notably, our algorithms for both models have asymptotically lower costs than the attacker's, as the attacker's costs grow large. Our algorithms use a simple rule to set required RB fees per job. We assume no prior knowledge of the number of jobs, the adversary's costs, or even the estimator's accuracy. However, these quantities parameterize the algorithms' costs. This is joint work with Trisha Chakraborty, Abir Islam, Valerie King, Daniel Rayborn, and Jared Saia.
4:15pm - (approx.) 5pm: Open Problem Forum
Dinner Location
After the workshop concludes, we'll walk over to Salt and Board for dinner at around 5:30pm. Afterwards, we will proceed to the nearby Flock of Moons brewery to verify the following study.
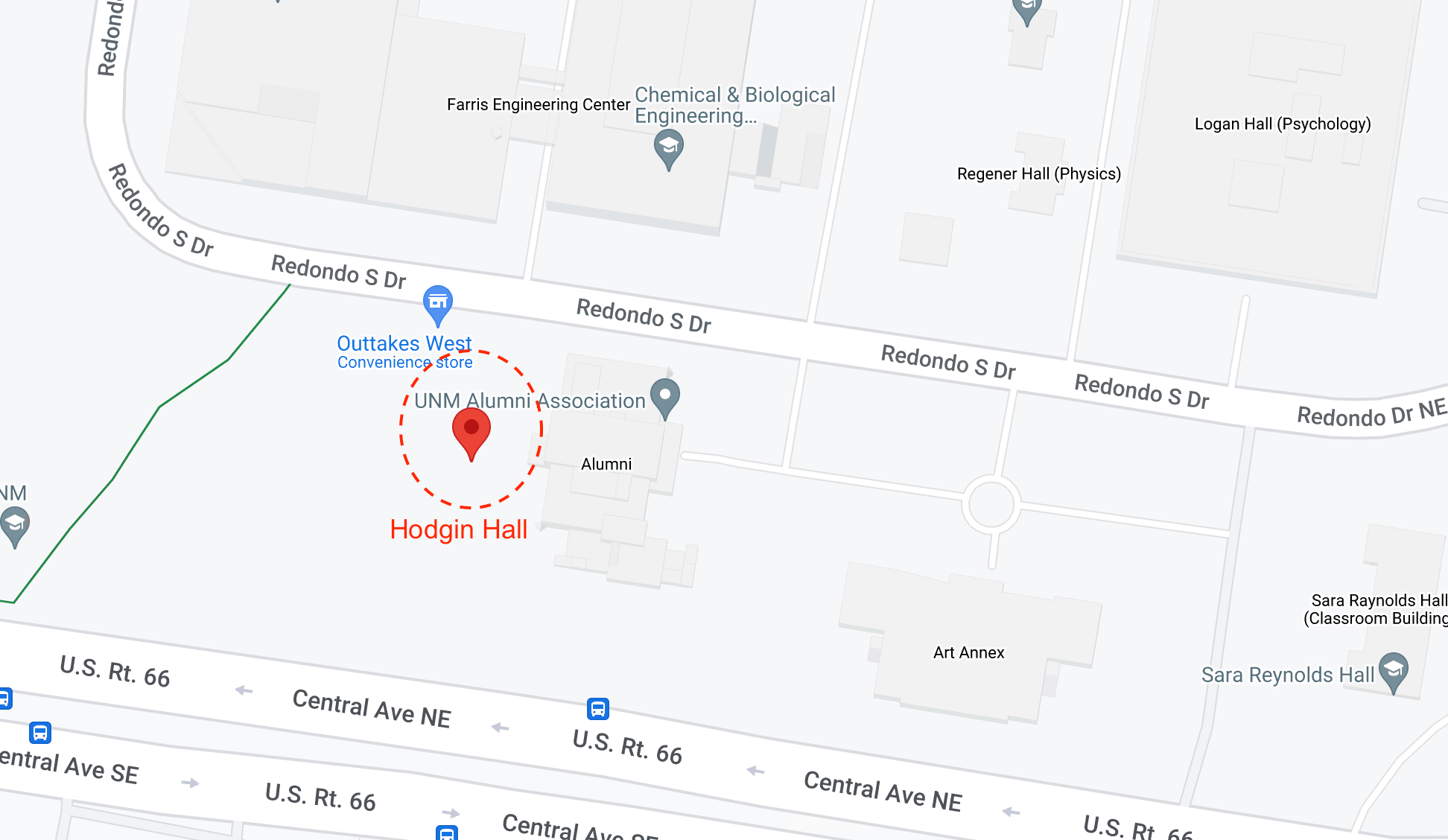
Workshop Location
This 1-day workshop will take place on UNM campus at Hodgin Hall in the Bobo Room.
Free parking is available in the Hodgin Hall Parking Lot; please enter Hodgin Hall to get a parking pass to display in your car.
List of Invited Speakers
Costas Busch Department of Computer and Cyber Sciences, Augusta University Varsha Dani Golisano College of Computing and Information Sciences, Rochester Institute of Technology Stephanie Forrest (Keynote Speaker) Biodesign Institute at Arizona State University Jacob Hobbs Department of Computer Science, University of New Mexico Aniket Kate Department of Computer Science, Purdue University Supra Valerie King Department of Computer Science, University of Victoria Carolyn D. Mayer Sandia National Laboratories Nick Pattengale Sandia National Laboratories Cynthia Phillips Sandia National Laboratories Peter Robinson Department of Computer and Cyber Sciences, Augusta University Gokarna Sharma Department of Computer Science, Kent State University

